Researchers are table to hijack a medical telerobot, raising questions around the security of remote surgery.
In a scenario that sounds straight out of a Hollywood thriller, researchers at the University of Washington have discovered a flaw in surgical robotic arms that allows them to be easily hacked. The experts were able to take control of a Raven II telerobot through a series of cyber attacks, thereby enabling them to change the speed of the arms of the robot and their orientation, making it impossible for the machines to carry out a procedure as directed.
The first successful telesurgery took place back in 2001 when a doctor in New York completed a gall bladder surgery of a patient 3,700 miles away in France, and since then, long-distance robotic surgery has taken off. Though robotic surgery has yet to become the industry standard, sales of medical robots are increasing by 20% each year. Meaning, vulnerabilities can certainly wreak havoc on operations should the proper security measures not be implemented.
In the case of Raven II, a remote operator uses two winglike arms to perform complex procedures where otherwise their hands might not be capable. While this experiment was performed in a controlled environment and not on the operating table, it’s apparent that more stringent security measures be taken. Raven II runs on a single PC, and communicates with a control console using a standard communications protocol known as Interoperable Telesurgery Protocol. But rather than take place over a secure private channel, commands are sent over public networks instead — and therein lies the potential risk.
For their study, the team performed various types of cyberattacks to see just how easily the arm could be disrupted. This included changing the commands sent by an operator, modifying signals and even completely taking over the robot. The researchers note that while their test applies only to Raven II, other surgical mechanisms that use similar teleoperation were likely also at risk.
“In hijacking attacks, a malicious entity causes the robot to completely ignore the intentions of a surgeon, and to instead perform some other, potentially harmful actions. Some possible attacks includes both temporary and permanent takeovers of the robot, and depending on the actions executed by the robot after being hijacked, these attacks can be either very discreet or very noticeable,” the team writes.
Since surgery requires the upmost precision, any minor glitch at a critical moment could prove to be deadly for a patient. Subsequently, researchers suggest a number of ways that telesurgery can be more secure, including encrypting data as it’s transferred from surgeon to robot, making the software more sensitive to errors and attempted data changes, and better monitoring of the network status before and during surgery.
“Some of these attacks could have easily been prevented by using well-established and readily-available security mechanisms, including encryption and authentication,” the researchers note.
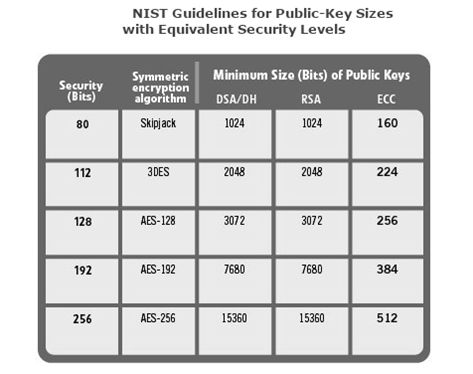
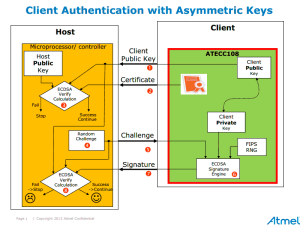
It’s becoming increasingly clear that embedded system insecurity affects everyone, and not only can these effects of insecurity lead to sensitive financial and medical data theft, but in some cases, could even lead to greater harm or fatality. This is why CryptoAuthentication protection is so paramount. As Atmel resident security expert Bill Boldt explains, “Hardware protection beats software protection every time. That is because software is always subject to bugs, tampering and malware, just as these attacks are proving. Again and again and again.”
Want to learn more? Download the entire paper here.