The most cost-effective and secure way to keep things real is through symmetric authentication without secret storage on the host using a fixed challenge.
With the ever present threat of counterfeiting, having a cost-effective and highly-secure way to ensure that a consumable product is real is a great idea. In fact, there is a proven industry standard approach to apply sophisticated cryptographic engineering and mathematics to fight counterfeiting; namely, crypto elements like the Atmel ATSHA204A device.
Crypto elements can attach to a consumable good, such as the classic example of an ink cartridge, even without being soldered in. The device can be glued directly outside of the product. When the ink or other consumable is inserted into the host system (where the MCU is), the crypto element makes contact and the host is able to communicate with the item to validate whether or not it is real. This is called authentication.
The most cost-effective yet secure way to authenticate is through symmetric authentication without secret storage on the host using a fixed challenge.
With symmetric authentication, a client and the host run the exact same calculation on each side, and if the client (the consumable) is real, then the results of those calculations (called the “responses”) will match. There is a way to go about using a very inexpensive MCU without running the crypto calculations within the host side’s MCU. That is where the concept of fixed challenge comes into play. The idea of a fixed challenge is that the calculation done for the host is conducted ahead of time, and the challenge/response pair from that calculation is loaded into the host.
The fixed challenge method is ideal when certain considerations are in play, such as the folowing:
- Very limited processing power (e.g. low-cost MCU)
- Abundance of available memory to easily store challenge-response pairs (e.g. in a smartphone)
- Need to get something out quickly or temporarily (e.g. time to market)
- Need a very low cost on the host (e.g. can’t afford adding a key storage device)
- Desire to not store a secret key in the host
So, how does a fixed challenge work? Like with other challenge-response operations, the process starts with the host controller sending the client a numerical challenge to be used in a calculation to create a response, which then gets compared to a “response” number in the host. What makes this “fixed” is that, because there is no crypto device in the host to generate random numbers (or make digests using hashing algorithms), the challenge cannot be random. That means that the challenges and their corresponding responses must be pre-calculated using the client’s secret key and the challenge and response pair loaded into the memory of the host. This can be looked at as effectively time-shifting the calculations used for authentication.
Let’s look at an example using the ATSHA204A installed in the client.
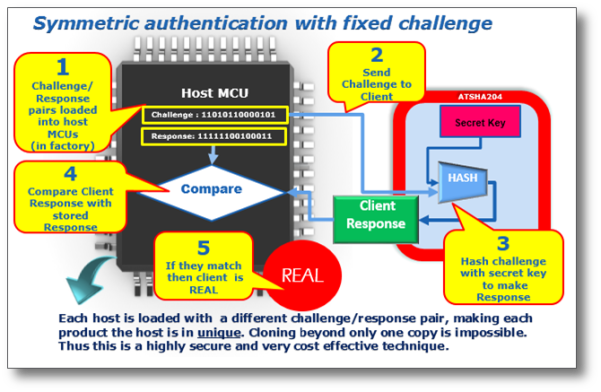
Step 1: In the factory when the host manufactured challenges are loaded into the host MCU memory together with a response that is calculated by hashing the client’s secret with that challenge.
Step 2: When the consumable is inserted into the host machine out in the field, the host MCU will ask the client (consumable) to prove it is real by sending it the preloaded challenge.
Step 3: The client will then run the hash algorithm on that challenge number using its stored secret key to generate a response, which it sends back to the host.
Step 4: The host will compare the response from the clients with the preloaded response value stored in its memory.
Step 5: If the client is real, the response from the client (which is the hash value based on the secret key and the challenge) will be the same as the response value that was preloaded in the host.
Since each host is loaded with a different challenge/response pair, each product that the host is incorporated into is then unique by definition. Cloning beyond only one copy is impossible; thus, this is a highly-secure and very cost-effective technique as it can be easily implemented with very inexpensive MCUs.
This approach can be used for firmware protection and designs with no secrets in the host (as noted), as well as be implemented with very low-cost MCUs that do not have the processing power to run the hashing algorithms.
The many benefits of fixed challenge authentication:
- Symmetric authentication is fast
- No secrets in the host
- Can use low-cost MCU of host because less computation is needed for a fixed challenge
- Prevents cloning
- Protects investments in firmware
- Enhances safety
- Protects revenue stream
- Protects brand image
- Better control of the supply channel
Atmel crypto element devices — including ATSHA204A, ATECC108A, ATECC508A and ATAES132A — implement hardware-based key storage, which is much stronger than software based storage due to the defense mechanisms that only hardware can provide against attacks. Secure storage in hardware beats storage in software every time. Adding secure key storage is an inexpensive, easy, and ultra-secure way to protect firmware, software, and hardware products from cloning, counterfeiting, hacking, and other malicious threats.