Taking a closer look at how ATECC508A CryptoAuthentication devices can help in providing robust authentication.
Forward secrecy, which is often referred to as Perfect Forward Secrecy (PFS), is essentially the protection of ciphertext with respect to time and changes in security of your cryptographic session keys and/or primary keying material over time.
A cryptographic session key is used to authenticate messages and encrypt text into ciphertext before it is transmitted. This thwarts a “man in the middle” from understanding the message and/or altering that message. These keys are derived from primary keying material. In the case of Public Key Cryptography, this would be the private key.
Unless you are implementing your own security in the application layer, you probably rely on the TLS/SSL in the transport layer.
The Problem
One can envision a scenario in which ciphertext was recorded by an eavesdropper over time. For a variety of reasons out of your control, your session keys and/or primary keying material are eventually discovered and this eavesdropper could decipher all of those recorded transmissions.
Release of your secret keys could be the result of a deliberate act, as with a bribe, a disgruntled employee, or even someone thinking they are “doing the right thing” by exposing your secrets. Or, it could be the result of an unwitting transgression from protocol. Equipment could be decommissioned and disposed of improperly. The hard drives could be recovered using the infamous dumpster dive attack methodology, thus exposing your secrets.
If you rely solely on transport layer security, your security could be challenged knowingly or unknowingly by third parties controlling the servers you communicate with. Recently leaked NSA documents shows powerful government agencies can (and do) record ciphertext. Depending on how clever or influential your snoopers are, they could manipulate the server system against you.
There are many ways your forward security could be compromised at the server level, including server managers unwittingly compromise it due to bad practices, inadequate cipher suites, leaving session keys on the server too long, the use of resumption mechanisms, among countless others.
Let’s just say there are many, many ways the security of your session keys and/or primary keying material could eventually be compromised. It only takes one of them. Nevertheless, the damage is irreversible and the result is the same: Those recorded ciphertext transmissions are now open to unintended parties.
The Solution
You can wipe out much of your liability by simply changing where encryption takes place. If encryption and forward secrecy are addressed in the application layer, session keys will have no relationship with the server, thereby sidestepping server based liabilities.This, of course, does not imply transport layer security should be discarded.
A public/private key system demonstrates the property of forward secrecy if it creates new key pairs for communication sessions. These key pairs are generated on an as-needed basis and are destroyed after a single use. Their generation must be truly random. In fact, they cannot be the result of a deterministic algorithm. Once a session key is derived from the public/private key pair, that key pair must not be reused.
Atmel’s newly-revealed ATECC508A CryptoAuthentication device meets this set of criteria. It has the ability to generate new key pairs using a high quality truly random number generator. Furthermore, the ATECC508A supports ECDH, a method to spawn a cryptographic session key by knowing the public key of the recipient. When these spawned session keys are purposely short-lived, or ephemeral, the process is known as ECDHE.
Using this method, each communication session has its own unique keying material. Any compromise of this material only compromises that one transmission. The secrecy of all other transmissions remains secure.
The Need for Robust Authentication
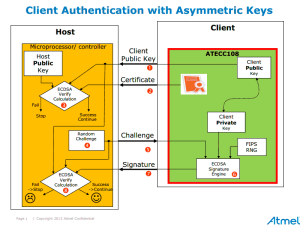
Before any of the aforementioned instances can occur, the identity of the correspondents needs to be robustly authenticated. Their identities need to be assured without doubt (non-repudiation), because accepting an unknown public key without robust authentication of origin could authorize an attacker as a valid user. Atmel’s ATECC508A provides this required level of authentication and non-repudiation.
Not only is the ATECC508A a cost-effective asymmetric authentication engine available in a tiny package, it is super easy to design in and ultra-secure. Moreover, it offers protective hardware key storage on-board as well a built-in ECC cryptographic block for ECDSA and ECDH(E), a high quality random number generator, a monotonic counter, and unique serial number.
With security at its core, the Atmel CryptoAuthentication lineup is equipped with active defenses, such as an active shield protecting the entire device, tamper monitors and an active power supply circuit which disallows the ability to “listen” for bits changing. The ECC-based solutions offer an external tamper pin, so unauthorized opening of your product can be detected.